This Week in Matrix 2019-07-12
12.07.2019 00:00 — This Week in Matrix — Ben ParsonsMatrix Live: RiotX
Nice! Manu and Benoit, who work on the Riot Mobile, discuss the development status of RiotX.
Dept of Servers 🏢
Synapse
A bit of everything this week, we’ve made changes to support the upcoming edits and reactions release, worked on soft log out, experimented with improving general perf for small homeservers, landed open tracing support, improved db query load.
Next week we’ll see about landing the small homeserver perf improvements, work on id hashing in sydent, fix some e2ee bugs (made easier to track down with OpenTracing), do some more database performance work and start gradually rolling out the new Sygnal instance.
Construct
Jason back on it:
This week in Matrix, Construct made the crazy-loading mode of client sync the default. Crazy-loading is an approach to initial sync that goes beyond lazy-loading for a better UX. It's even backwards compatible with clients that don't support lazy-loading.
Construct also made significant progress on implementing version 3 and 4 rooms during the week. This is nearly complete, and should be ready for testing by the weekend.
Good to know there is progress with new room versions as more and more rooms start to be moved over to v4. #zemos-test:matrix.org for testing and more info.
Dendrite
This week we’ve implemented profile retrieval over federation, single event retrieval, room tagging as well as host of bug fixes.
Next week we’ll be looking at state resolution and implementing our latest and greatest algorithm needed by modern room versions.
This Week in Ruma
Jimmy provided This Week in Ruma:
Work continues on the major revamp of ruma-events mentioned in the last update.
...
There are also a few modules that are somewhat blocked on an issue in ring. Some of the types in ruma-events contain types from ruma-signatures which don't implement Clone and PartialEq because they contain types from ring which don't.
...
Rust 1.36 was released, and it includes stabilization of the Future trait, one of the long-awaited building blocks for first-class async support in Rust. [...] the biggest reason for Ruma's development hiatus is waiting for async networking in Rust to mature, and this is one of the final pieces of foundational support we've been waiting for. The remaining pieces are async/await syntax, which is expected in either the next version or the one following it, and finally, waiting for important libraries like Hyper and Tokio, as well as web frameworks, to adopt the new stuff.
Dept of SDKs and Frameworks 🏗
libQuotient gets .well-known support
Thanks to Black Hat, libQuotient gained support of .well-known - a very useful feature to connect to Modular-hosted homeservers!
Also, the first block of E2EE functionality from aa13q has been merged to libQuotient master - so far it's just uploading the keys but receiving messages is already well in the works!
Dept of Bridges 🌉
mautrix-telegram v0.6.0
mautrix-telegram v0.6.0 was released. Recent changes include bridging strikethrough, underline and nested formatting to telegram and some bug fixes, including one security fix. Full changelog on GitHub.
Debian 10 was also released recently, which means v0.6 is the last version with Python 3.5 support. Starting from v0.7.0, mautrix-telegram will only support Python 3.6 and up.
mautrix-telegram v0.6.0 also includes Native Matrix edit support, message editing between platforms.
matrix-appservice-slack 0.3.0-rc2
Half-Shot and the Slack-bridge-gang have announced matrix-appservice-slack 0.3.0-rc2
Hi folks, the slack bridge has had another RC release this week 0.3.0-rc2 which has been deployed onto matrix.org :). In other news, we are nearly done with the port of the bridge to Typescript (slated for the 0.4 release) which has allowed us to clean up the codebase significantly and splat a lot of bugs.
I'm for any movement toward TypeScript - seems to be a winner in the JS-world. Says Half-Shot:
I'm a bit fanatical about Typescript, it's objectively better to write things in TS than JS if you have the freedom to do so. It's also allowed us to keep the bug count down on the Discord bridge, so I'm starting to look at the other bridges for typescript support too.
Reliable Bridges GSoC project 🎓
Thanks Kai for this update!
The new Spec proposal MSC2162: Signaling Errors at Bridges landed! It is about adding permanent errors: The ability of bridges to mark events as not delivered to all participants. While there is already code supporting the feature, the Spec process is important for getting everyone on board and finding potential problems with the current approach.
In spite of being a relatively small proposal, there were already a lot of suggestions and directions in which it can evolve. Shoutout and thanks to everyone who already contributed to it with their comments!
Meanwhile on the more practical front a fork of Riot Web was extended to now support the actual visual display of bridge error markings on messages.
See it in action:

Dept of Clients 📱
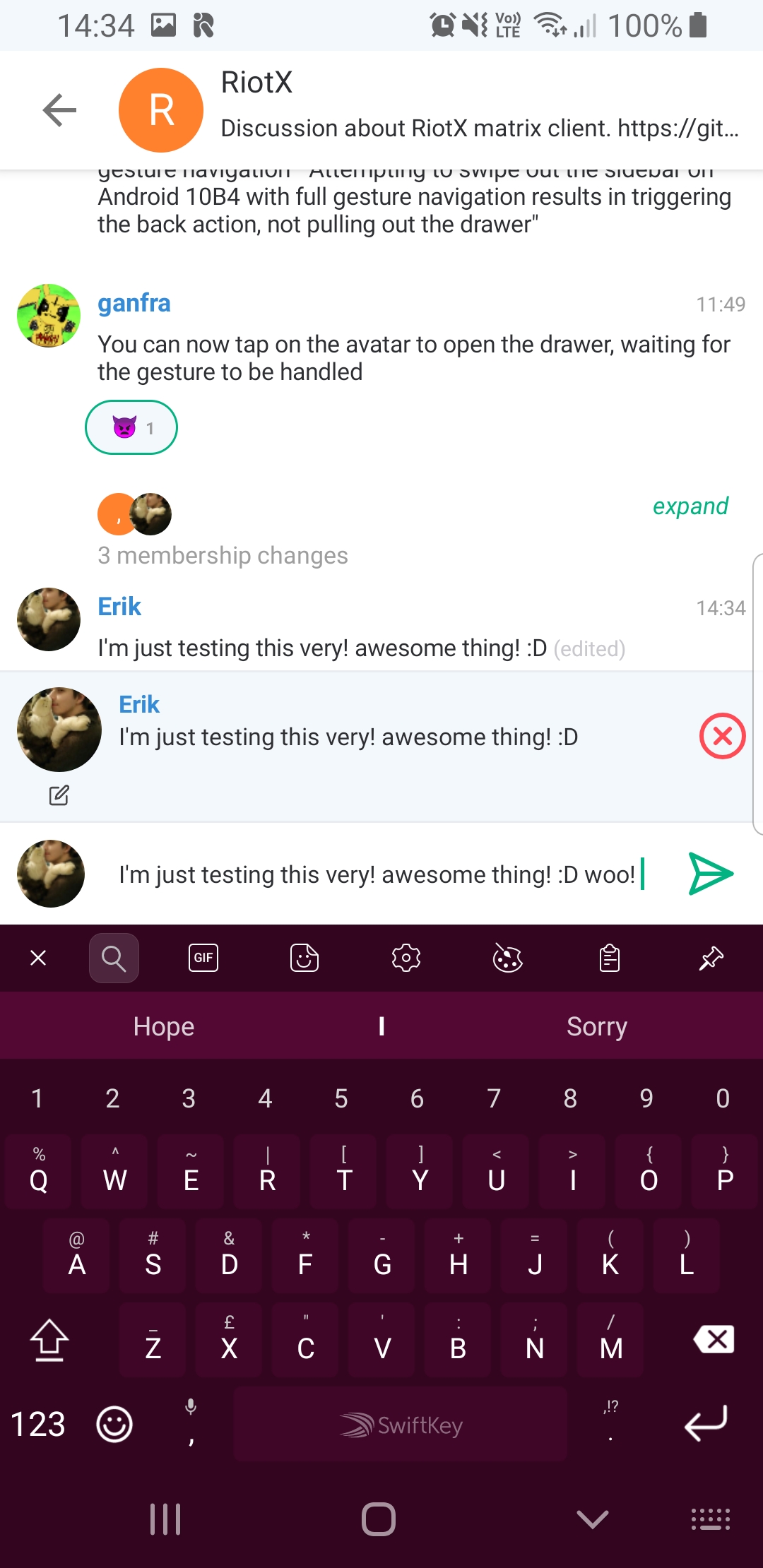
RiotX big announcement!
- We have released a beta version to the PlayStore on Thursday! You can download (and rate it) here: https://play.google.com/store/apps/details?id=im.vector.riotx . Also feel free to join https://matrix.to/#/#riotx:matrix.org to provide any feedback!
- You will find more details about what RiotX can (and cannot yet) do here: https://medium.com/@RiotChat/introducing-the-riotx-beta-for-android-b17952e8f771
- Now we are working on fixing bugs, and keep going implementing the missing features
I've been using RiotX a lot lately and find it great - really snappy.
Spectral
Spectral supports .well-known now obviously. see libQuotient update above
Also a lot of changes:
- Bubble shapes for pending events are fixed.
- You can set device name when logging in. This becomes important as libQuotient begins to upload one-time device key as part of E2EE implementation.
- Markdown is parsed automatically by default, and works with replies.
- Small UI improvements in timeline and room list.
Continuum
yuforia has continued work on Continuum, a desktop client written in Kotlin:
Continuum now preserves media content URI (mxc://) internally in order to treat them specially, instead of converting to all URI to http (or https) upon receiving.
This week's version never considers cached mxc resources stale and no network request will be performed for refreshing.
Continuum also loads previews for http image links in text messages automatically. The usual http cache control rules are still followed in those cases.
Join #tkmc:matrix.org to chat more about Continuum, or about koma, the underlying library.
Riot Web
Riot v1.3.0-rc.1 is now ready for testing at https://riot.im/staging. This includes some last minute polish of reactions and edits, and also adds initial support for soft logout. This release will have reactions and message editing enabled via configuration on riot.im once it stabilises.
Self-hosted installs that wish to do the same would need to alter their config.json in similar fashion. This is because these features currently depend on unstable APIs, and we don't want to move them out of labs and fully on by default until that is resolved.
Riot iOS
- Reactions and edits:
- Enabled by default (no more LABS setting)
- Reactions with non-unicode keys
- Original event in the edit history (need homeserver update)
- Upgraded rooms are now autojoined when tapping on the upgraded banner
- File upload from the room screen and from the share extension
- Crypto: logs have been improved and a script has been created to help to debug e2e bugs (see the screenshot at https://github.com/matrix-org/matrix-ios-sdk/pull/692)
- This Friday TestFlight can be considered as a release candidate
Dept of Ops 🛠
matrix-docker-ansible-deploy: synapse-janitor now available
Thanks to Aaron's frequent mention of synapse-janitor and other such cleanup methods, I've finally gotten inspired enough to give it a try.
The playbook now contains a new Synapse Maintenance documentation page and an easy/safe way to run synapse-janitor.
To give an example, using synapse-janitor and a full Postgres
VACUUMyielded a 29% reduction in disk space used by Postgres on my personal homeserver (5.3GB -> 3.8GB).
Alexey Murz Korepov also reminded us about synapse-purge, which we've mentioned here before - but is designed for a similar purpose.
avhost/docker-matrix
the avhost/docker-matrix image has moved to a debian buster base image, which got us an upgrade from python 3.5 to python 3.7.3 and jemalloc1 to jemalloc2, which should improve the performance of synapse.
Dept of Articles 📝
Pneumaticat: "wrote a blog post on integrating Riot chat with our dapp & scientific research auditing platform, Delphus!"
Final thoughts 💭
I had/stole the idea to create a bot which uses message edits to send frames of an ASCII-art animation. I indeed created the bot, which works to a degree, but is quickly punished by rate-limiting, which limits the effectiveness. Still it's quite fun, you can check out the code here.
TravisR's work on matrix-bot-sdk is interesting for bot or other client devs, and there is a new guide available: http://matrix.org/docs/guides/usage-of-matrix-bot-sdk
A few weeks ago I mentioned matrix-enact, which uses Web Audio API to play back room history. There is a guide to how it was built, looking at the /context endpoint now available: https://matrix.org/docs/guides/creating-a-simple-read-only-matrix-client
Half-Shot "bridged #synapse:matrix.org to #matrix-synapse on freenode to help folks who might be experiencing issues with their homeserver and need a IRC based support channel"
Black Hat made a cool-looking thing: "It basically shows all pictures in this room in a waterfall, with 'infinite scroll'"
That's all I know 🏁
See you next week, and be sure to stop by #twim:matrix.org with your updates!